TECHD’ Self Help Section (FAQ)
Blurb
TECHD RMM is a remote monitoring and management (RMM) platform that enables our employees to remotely manage and monitor our clients’ IT infrastructure. It provides a single console for monitoring and managing all devices, applications, and networks, making it easier for our teams to identify and resolve issues before they become major problems.
Here are some of the ways TECHD RMM benefit companys:
Proactive Monitoring: TECHD RMM enables our internal teams to proactively monitor devices, applications, and networks in real-time. It provides alerts for potential issues, such as low disk space, antivirus alerts, and failed backups, so we can resolve issues before they impact end-users.
Remote Management: TECHD RMM enables us to remotely manage devices and applications from a single console. We can deploy software, apply patches, and configure settings without needing to interrupt the end-users device*
Automation: TECHD RMM includes a range of automation tools, such as scripting and policy-based management, that our internal teams to automate repetitive tasks and reduce manual intervention.
Security: TECHD RMM includes a range of security features, such as antivirus, ransomware protection, and patch management, that help protect devices and data from potential security threats.
Reporting: TECHD RMM provides detailed reporting on device performance, security events, and software usage. This enables our internal teams to identify trends and make data-driven decisions.
Overall, TECHD RMM benefits companys by enabling to monitor and manage our clients’ IT infrastructure more efficiently and proactively. This can help reduce downtime, improve security, and ultimately provide a better end-user experience.
*End-User Privacy
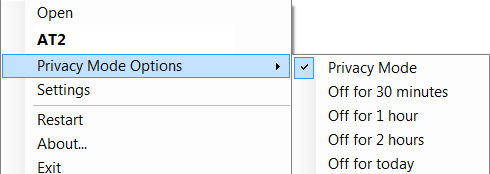
Privacy mode is a feature designed to protect the privacy of end-users by preventing employees from accessing sensitive data on end-users devices. When Privacy mode is enabled, employees cannot remotely access files or applications on a device, nor can they view the device’s screen or take control of the mouse and keyboard.
Privacy mode is enabled by default for all devices managed by TECHD, and it can only be disabled by an authorized user with administrative privileges. However, even with Privacy mode disabled, IT employees cannot access sensitive data on a device without the user’s explicit approval.
When an employee attempts to access a device that has Privacy mode enabled, the end-user will be prompted to either allow or deny access. If the end-user denies access, the IT employee will be unable to access any data on the device until the end-user approves the request. This provides an additional layer of security and ensures that sensitive data is not accessed without the user’s consent
Privacy Mode can be disabled/enabled by the end user on the device Once Privacy Mode is enabled, it can only be disabled by the end user on the device itself.
*Note Privacy mode can not be disabled on MacOS Devices. All actions will require end-user physically approval.
Public Wi-Fi
Joining the complimentary Wi-Fi
See Wi-Fi terms and conditions.
Please note that this free Wi-Fi service is not encrypted.
To make joining the Wi-Fi as easy as possible, we recommend:
- ensuring you have the latest operating system on your device
- clearing browser cookies and cache
- turning ON cookies from visited websites
- turning OFF private browsing
- setting your IP address settings to automatic
- selecting ‘Mapletree Public WiFi’ as your connection network.